Cloud Detection And Response Tools Do Not Exist
My colleagues Andras Cser, Jeff Pollard, and I recently released new research on a hot topic: cloud detection and response. In our report, The Comprehensive Guide To Cloud Detection And Response, we define cloud detection and response as:
The detection of and response to cyberattacks on detection surfaces in the cloud control plane, data plane, and management plane. This includes one or more cloud-native tools that prioritize security analyst experience for high-quality detection, complete investigation, and fast and effective response to cloud attacks.
This definition is important for a few reasons: First, it calls out that “cloud detection and response” products are not a single tool or service. There are many tools that incorporate cloud detection and response as part of what they do, but the vast majority started on the structural awareness side with configuration and vulnerability management.
Cloud detection and response is not a market category — it is a feature of existing cloud tools, including cloud workload security (comprised of cloud security posture management, cloud infrastructure entitlement management, cloud workload protection, container security, infrastructure-as-code scanning, and other solutions).
Cloud detection and response is split into three detection surfaces:
- Control plane. The control plane provides the functions used to create, read, update, delete, and list (CRUDL) resources. Cloud detection and response in this plane relies on tools provided by the cloud infrastructure service provider in IaaS or PaaS. Detections on this surface come from built-in tools such as AWS Guard Duty, Microsoft Defender for Cloud, and Google Cloud Security Command Center or from detection engineering on AWS CloudTrail, Microsoft Azure, or Google Cloud Audit logs.
- Data plane. The data plane provides the primary function of the service. It is effectively what is managed by the end user. Detections on this surface come from a workload deployed on a cloud service, such as the operating system, virtual machine, container, or data stores, which can be done via logs or through tools like cloud workload security.
- Management plane. The management plane provides the higher-level aspects of data and configuration. It is effectively what can be managed within a third-party application (such as a SaaS application). Detections on this surface come from third-party applications, such as commonly used enterprise tools like Duo Security, GitLab, Microsoft 365, Okta, or Salesforce.
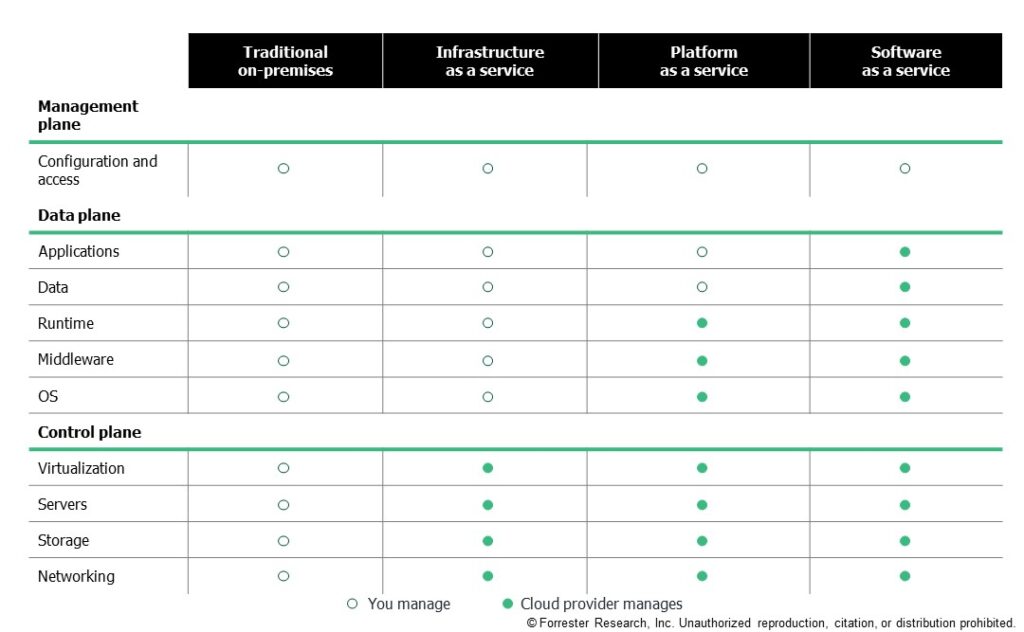
This framing helps security pros identify what control they have based on the type of cloud service they are delivered. In different planes, different detection surfaces exist, different levels of visibility are available, and different response actions can be taken. Without this perspective, it can be difficult to bucket detection technologies and response activities appropriately.
We’ve got a lot more detail covered in the full report, which Forrester clients can read here. Forrester clients can also chat with Andras, Jeff, or me via inquiry or guidance session.
