IoT, IIoT, IoMT, And OT — Welcome To Acronym Mania. What Does It All Mean?
Across IT, acronyms come with the territory. Whether they’re classic ones (ENIAC, Electronic Numerical Integrator and Computer), just a tad more modern (VAX, Virtual Address eXtension), network-based (TCP/IP, Transmission Control Protocol/Internet Protocol; XNS, Xerox Network Systems), or cybersecurity-related (NGAV, next-gen antivirus; DLP, data loss prevention; IDS, intrusion detection system), the acronyms and the process of keeping up with them are endless. It doesn’t help that many IT vendors create new acronyms in an effort to stand out and make themselves feel special.
In the world of autonomous endpoints, we are dealing with five primary acronyms. To clarify the meaning of these acronyms, here is some guidance and perspective.
IoT: internet of things
This is the broadest category, as there are a myriad of devices and technologies within it, both at home or as part of a business. Device types range from smart assistants, doorbell cameras, and fitness trackers to printers, security door locks, and warehouse label scanners. What ties these devices together is that they are designed to communicate and exchange internet data, with ‘I’ being the key letter in the acronym. IoT devices, such as sensors and actuators, are integrated into or attached to machines or assets and connected to the internet via a Wi-Fi connection or through cellular networks. The devices use cloud platforms to send and receive data to make informed decisions about the connected assets.
IIoT: industrial internet of things
A subset of the IoT category, these devices, as the name implies, are made for heavy work but are often larger than simple sensors or scanners. IIoT devices are usually focused on improving industrial processes, including predictive maintenance, asset tracking, quality monitoring, process optimization, supply chain visibility, and building management. The industrial aspect isn’t restrictive to just monitoring; it can also incorporate devices such as electric vehicle chargers or building management systems. The first ‘I’ is the differentiator in the acronym.
OT: operational technology
As the name implies, OT encompasses the hardware and software that controls the physical operation of industrial devices. Here is where we will find manufacturing, energy production and transmission, water treatment devices, or factory equipment. Connectivity is regularly restricted to private networks, but in recent years, OT has started to have external/internet connections. The focus is on the ‘O.’
To make matters worse, under OT, you also have industrial control system (ICS), supervisory control and data acquisition (SCADA), distributed control systems (DCS), and programmable logic controllers (PLC). There seems to be no end to OT-based acronyms.
IoMT: internet of medical things
As the ‘M’ implies, this subset of IoT revolves around devices used within the healthcare industry. These could be devices in a hospital, such as infusion pumps or smart medication dispensers, or outside devices like blood pressure monitors, CPAP machines, and pacemakers. But like IIoT, you also have devices that could be considered operational technology like MRI or X-ray machines, but it is generally accepted that IoMT, the ‘M’ for medical being the distinction, will incorporate both IoT and OT.
M2M: machine to machine
This entails technology that enables machines to interact via wireless or wired communication channels without human intervention. Devices connect and interact with each other to exchange information and perform actions without requiring an internet connection. M2M technology is often integrated into security, track and trace, automation, manufacturing, and facility management processes. IoT technology differs from M2M communication because IoT extends interactions to include cloud-based networks.
Please note: We recognize that there are many other relevant IoT-related acronyms, which we will explore in an upcoming IoT report.
A simplified version that takes these distinctions to just IoT and OT would be: IoT devices are those that you run inside your business. If these devices go offline, you may have some challenges, but your business can still function. OT devices are those that run your business. If these devices go offline, you’re not doing business.
Like all analogies, there are exceptions that don’t fit. For instance, if your medical business relies on performing MRI scans and the MRI machine is offline, you can’t do business. A hospital can treat patients without IoT infusion pumps or Bluetooth pulse oximeter sensors, but it won’t be easy. And would you really want to run your industrial manufacturing tools without IoT noxious gas sensors? For a little more distinction, we could use this image below:
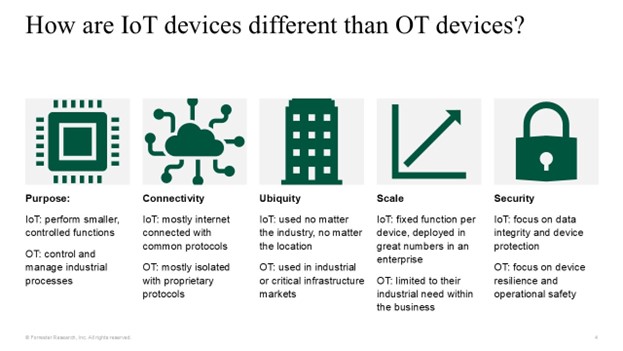
Device protection is important with IoT and OT, but the purpose is different. For IoT devices, the goal is to protect the data. For OT, the goal is maintaining operational safety. Because of this, the approaches to security for these technologies have historically been different. Until recently, many enterprises completely walled off their OT devices into their own air-gapped network, developing extensive human-action security policies to control the flow of data in and out of the network to ensure that these devices stayed operational and weren’t exposed to internal or external threats. Conversely, IoT devices were often interspersed throughout the enterprise with other endpoints. In more secure environments, network traffic to and from these devices is logically segmented and controlled to protect them against internet-based threats.
Security in IoT and OT environments is currently changing. The walls between the OT devices and the rest of the network are becoming porous. Business leaders are still highly concerned about OT security, but the need for connectivity to IT and internet resources is growing. For IoT, simple segmentation is no longer sufficient because of the mounting threats. This is leading business and security leaders to deploy solutions to improve device security.
New acronyms will continue to emerge (such as the confusing CPS, cyber physical security) as IoT and OT security solutions expand. I’m still dreading hearing about the first IoTDR solution. Vendors in this space need to stop throwing out word salad in an attempt to make something relevant and stick with established acronyms.
If you’d like to get assistance in understanding the complexities of managing and securing IoT and OT devices, please schedule an inquiry or guidance session and we’ll discuss these matters further. In a series of reports (such as The Forrester Tech Tide™: Internet Of Things, Q1 2025) that are included in an IoT solutions-focused wave of research, Michele Pelino and I will continue to address these topics and others to assist you in identifying, piloting, developing, and deploying IoT use case initiatives as well as those of other enabling technologies.
